IT for Revenue

Companies like yours are investing in IT, however, poorly executed or under-planned tasks waste money. In contrast, those that plan and execute accurately get returns from their investments year after year. How can you do the same? It all starts with recognizing how IT increases the value within your company. Here are 3 valuable processes […]
Does IT Save You Money?

If your information technology isn’t saving you money, it’s time to change the way you leverage IT to cut costs and skyrocket revenue growth! Information technology can support the value creation processes of your organization, but first, you must know what value is: there are two types of value sources within your company – those […]
Do you have an appreciation for Information Technology?

You should respect and appreciate IT, because a secure network is the only thing protecting you from threats that have the potential to put you out of business. That sounds dramatic, but it’s true. Just one online security breach could cause enough damage to shut you down for good. There were over 300 million new […]
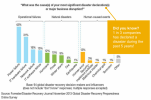
Only 3% of Data Loss Occurs Due to Natural Disaster… 97% Happens Because of Employees!

You’ve heard data loss horror stories before… but do you know how many ways data loss can occur? So many businesses still believe they’re not targets for cybercrime. Why spend money on solutions for something that’s not likely to happen? 86% of companies experience data loss! Think you’re not at risk? Think again! Here’s just […]
Data is Your Company Currency: Protecting Your Livelihood

An investment company came into the office early Monday morning and all their data was gone. The computers would not boot up, the screens were black. Company bank accounts and most employee’s bank accounts were emptied. Customer accounts had been transferred out of their control. Within a month, they were out of business. Twenty-eight people […]
Does IT Comply With Your Standards?
This article will show you how to hack into a network from inside the office, outside on the wireless and even break into your car. If it’s that easy, what are you doing to protect yourself and your company? So how do you ensure that your IT complies with your security standards? Controlled flexibility […]

